Earlier this week Intel and teams of researchers from around the world revealed the latest in a laundry-list of CPU vulnerabilities discovered since Meltdown and Spectre in 2018. These cache-based vulnerabilities opened up whole new avenues of research into the weaknesses of CPU micro-architecture, particularly branch-prediction algorithms, and Intel have been the chief victim. In fairness, as the dominant player in both customer and enterprise spaces, Intel has the largest target on its back and hence the most resources devoted to uncovering flaws, but that must come as scant comfort to customers and shareholders.
The new blemishes on Intel's record have been dubbed Microarchitectural Data Sampling (MDS) vulnerabilities, and are variants of speculative side-channel attacks. They analyse large quantities of data passing through intermediary buffers within the CPU, isolating repeating patterns that could correspond to secure data. Although it should be relatively difficult to target and isolate specific information using MDS attacks, frequently used data (such as hashed security keys) may be extrapolated from a large enough sample.
Select members of Intel 8th and 9th Generation CPUs incorporated hardware mitigations against this new type of attack, but prior generations require microcode and software updates to curtail their use. Researchers have also recommended that users disable Hyperthreading as a precaution, a measure immediately met with resistant from Intel due to the importance of Intel HT to overall CPU performance in enterprise and some consumer applications.
The performance impact of these measures on current generation CPUs, including disabling Hyperthreading, has now been documented by Intel.
According to their lab tests most applications are essentially unaffected, with only single-figure dips in perf. once MDS mitigations are applied. Taking the further step of also disabling hyperthreading saw a larger impact in synthetic Sysmark 2014SE and SPECint_rate_base 2017 (n copy) tests, as much as 9%. 3DMark Skydriver test results, in theory representative of gaming but much less gruelling a test than 3DMark FireStrike, differed only by 1%. This may also be a reflection of how poorly optimised for multi-threaded applications many consumer applications are.
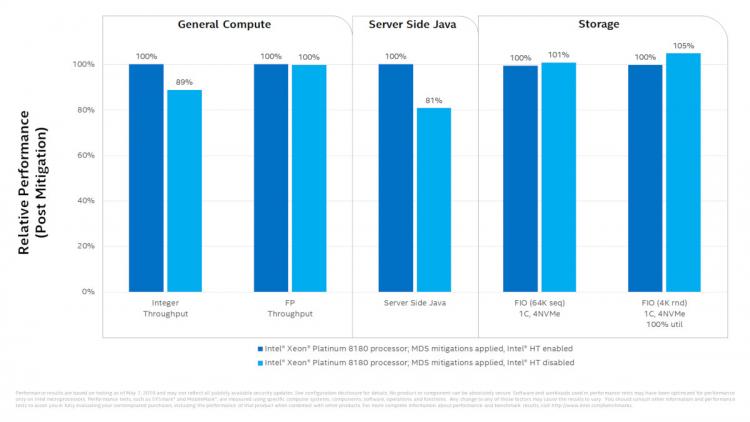
The tale was a little different for client and data-centre CPU workloads. Implementing the main MDS mitigations had little impact except in storage performance, but disabling Hyperthreading saw performance dip by as much as 19%. Integer throughput and server-side Java processing were particularly affected on a system powered by two Xeon Platinum 8180 processors (28 core, 2.5 GHz) of 2017 vintage. Just as with Meltdown and Spectre it appears that business customers have most to lose implementing the full range of mitigations.
It's important to note that the data revealed by Intel does not addresses applying the same fixes to consumer CPUs from prior generations.
At this time it's believed that AMD and ARM CPUs suffer from the architectural flaws that have allowed these attacks on Intel CPUs. Both are attempting to make inroads into Intel's market dominance, and these new vulnerabilities may well see businesses at least consider alternatives when they would previously have been rock-solid Intel customers.